Secure coding practices/techniques are necessary to mitigate vulnerabilities of codes. These practices need to be incorporated in building any computer application as insecure applications can expose users or other systems/sub-systems to many dangers. Among other practices sanitize input is one of the best practices that developers can use to ensure the external input/data are excluded of malicious codes and those data are in a harmless form.
Many programs receive unknown and un-trusted data from known or unknown sources like users, networks connections and other systems. Usually, these data are in the form of a string, probably according to a predefined structure. These data will pass into trusted domains for many purposes. Such data must be sanitized before they inserted into a subsystem as;
- Subsystem(s) may not be able to handle malicious input
- Non-sanitize input may include an injection attack
According to OWASP sanitizing data is one of the four strategies for validating data and if simply put sanitizing data/input means altering the input to an acceptable form to make sure that the input does not contain any harmful/malicious data.
There are two ways to sanitize input.
- Sanitize with whitelist – Remove/encode or replace powerful characters with harmless equivalents. Ex: the encoded version of the string ‘I like this bag’ will appear like “I+like+this+bag%21”
- Sanitize with blacklist – Escape or translate characters to make the input “safe” i.e. looking for powerful characters in a string and add escape characters before them.
A program code can be written without input sanitization procedures to make the code simple, but it would contain many vulnerabilities. Most of the injection attacks, ex: XSS attacks, SQL injection, LDAP injection and etc. can be executed through the codes written without any filters/ sanitizing functions. To avoid these attacks, programmers can use sanitization functions/ filters provided by different languages or use custom sanitization functions according to their needs.
Following simple PHP programme demonstrates how an attacker can perform an attack through the vulnerabilities of poorly written code (without sanitization practices) and how it can mitigate using PHP filters.
code in Fig_1 creates a small form to collect details from users; First name, Last name, e-mail address and comments.
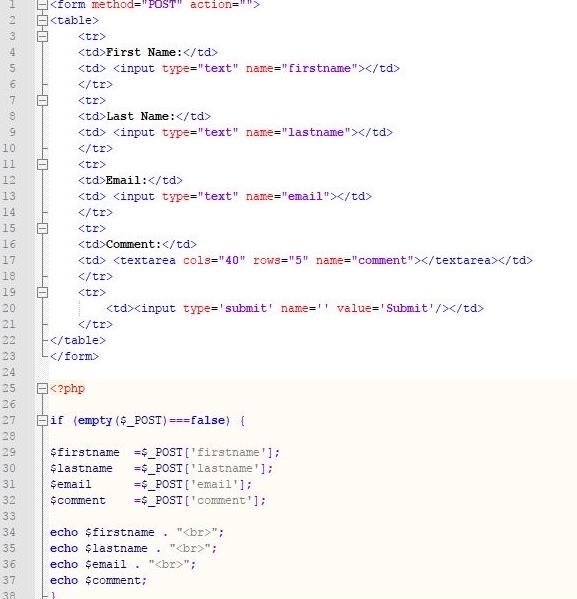
Fig_1: PHP code – without sanitizing filters
Fig_2 shows the data filled by a user and its output. This user provided harmless data, hence the data would not harm the database which it will be stored or other sub system(s) these data are intended to insert as an input.
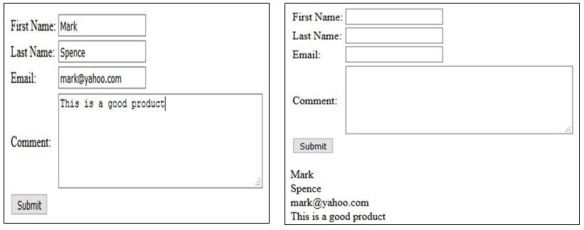
Fig_2 : User input and output
Fig_3 illustrates the input and output of another user . Since the form does not filter/sanitize user input this user able to alter the output by simply adding few codes to the data he/she entered. These data will not do any harm since they are harmless codes.
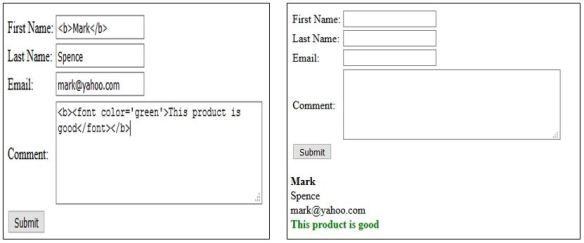
Fig_3 : User input and output
Assume someone with a destructive intention wanted to do a serious damage to the entire database or other subsystem(s) these data are intended to insert. To do so, he/she can simply use a harmful code with normal data. Since the code is not using any sanitizing methods, there is a possibility that person will be successful in his/her attempts. Following figure illustrates such an attack.
Fig_4 shows the input and output of another user. This user entered a simple script with normal data (alert(‘You’re terminated’)) and able to pop-up a message on the screen. This script can be advanced to an XSS attack or other injection attacks with a good knowledge of coding.

Fig_4 : User input and output
This vulnerability can be remediated through PHP filter functions.
Fig_5 shows the PHP code written with filters to sanitize First Name, Last Name, e-mail and comment fields. First Name and Last Name fields are sanitized using FILTER_SANITIZE_STRING filter which helps to removes tags and remove/encode special characters from a string. E-mail field is sanitized using FILTER_SANITIZE_EMAIL which is specially designed to remove all illegal characters from an email address. Comment field is sanitized using FILTER_SANITIZE_SPECIAL_CHARS which helps to escape special characters i.e. escape ” < > & and characters with ASCII value below 32.
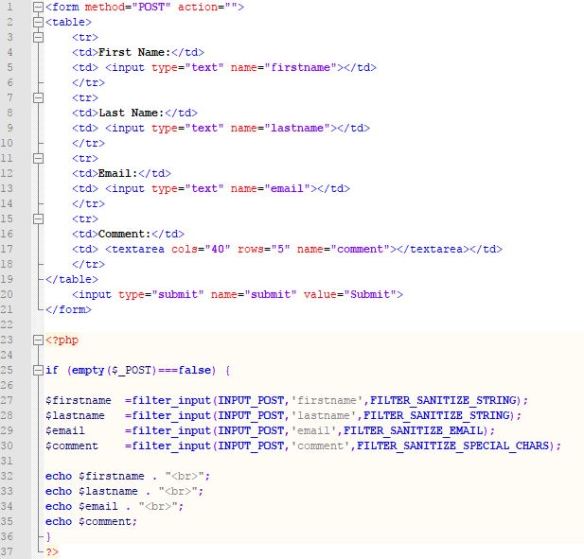
Fig_5 : PHP code with filter functions
Fig_6 shows that the output is neutralized and the script can no longer create a pop-up message on the screen or other html tags can alter the user input.

Fig_6 : User input and output
From the above simple example you can see that sanitizing user input is one of the best secure coding practices that can be easily and intentionally used to avoid security issues of coding. However, it is recommended to use sanitize data with other secure coding practices like validation and escape functions to provide in-depth security for applications.
